Four Ways to Secure Your Cell Phone While Protesting in Boston
Your rights and privacy are important. Put these digital safeguards into place before heading out to protest.
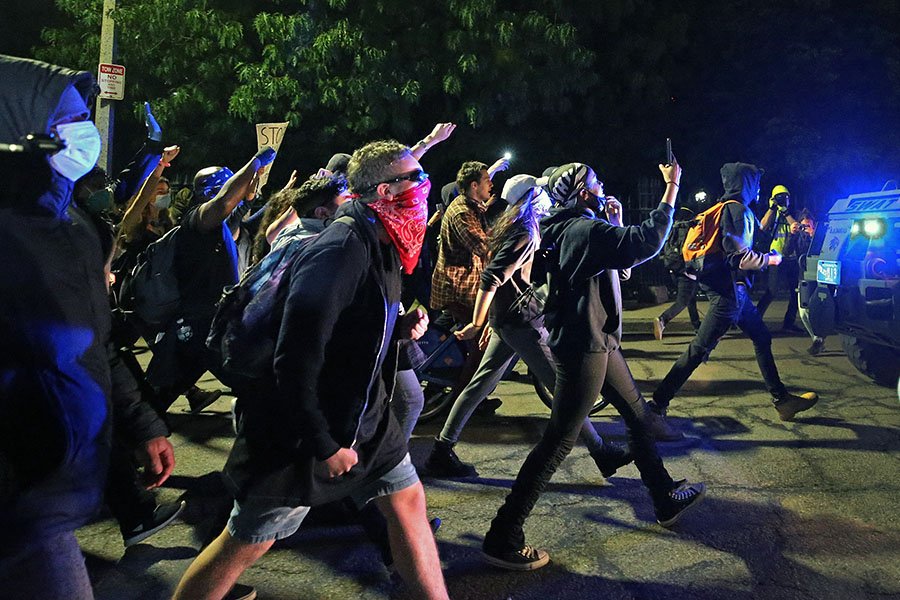
Photo via Getty Images/Boston Globe
By now, maybe you’ve pretty much resigned yourself to the idea that the information on your phone is not private. We click “agree” on terms and conditions without blinking (or reading), let our photos auto-backup to the cloud, and grant random apps access to our locations, contacts, and faces. But now, as thousands of Bostonians gather at demonstrations to protest police brutality against black people, bringing those insecure treasure troves of data into these gatherings can put yourself and others at risk by making movements trackable or compromising the privacy of vulnerable protestors, among other issues. Kade Crockford, the director of the Massachusetts ACLU’s Technology for Liberty Program, puts it simply: “Cell phones are notoriously insecure.” So, we asked for her advice on what steps we can take to protest safely while carrying a phone.
Leave your phone at home, if you can. The easiest and most reliable way of making sure that information from your phone isn’t compromised during a protest is to not bring it with you at all. If you’re going with another person, consider limiting the number of phones you bring, and deciding on a safe meeting point ahead of time if you were to get separated. But if leaving the house without a way to get in touch with anyone isn’t a practical solution for you, Crockford suggests an alternative: Keep your phone in a Faraday bag. The pouches, made of metallic fabric, can prevent police from remotely pulling data from your device. “But,” she cautions, “they block signals, so you won’t be able to accept messages or calls,” either.
Even keeping a powered-off phone in your pocket poses some degree of risk. “Very sophisticated groups like the NSA [National Security Agency] have the ability to activate a phone’s microphone and camera even when the device appears to be ‘off’,” Crockford says, though she admits it’s unlikely that local police have that capability. The bottom line: “If you are at high risk and you need to be 100 percent sure no one is tracking you or listening to you through your phone, leave it at home or put it in a Faraday bag,” she says.
If you need to text, use Signal. “People should not use plain text SMS messages,” warns Crockford. “This is the most insecure form of communication, as these messages can be plucked out of the air and read by the police if they are using sophisticated cell phone monitoring technologies known as IMSI-catchers.” Even after protesters have dispersed, police may “send demands to phone companies asking for the content of text messages,” she explains. The workaround? Download Signal, a free messaging app available on Androids and iPhones. The private messenger uses end-to-end encryption, rendering any intercepted texts unreadable and ensuring only the contact you sent the message to actually sees it. In sensitive situations or even in daily life, it’s a smart way to communicate. “I use Signal for everything, even birthday wishes and reminders to grab milk from the store,” says Crockford. “People ought to use encrypted messaging for all of their communications, not just sensitive ones.”
Set a strong password and adjust your settings. Make sure you’ve disabled face ID or thumbprint access on your phone before heading out so that you can’t be physically forced to unlock your home screen. Instead, Crockford recommends choosing a long password (at least six characters), but one that you can easily remember. Then, go into your settings and turn off location services for all apps. While you’re in settings, Google phone users need to turn on encryption; it’s worth noting that iPhones are encrypted by default. And, she adds, “Apple doesn’t make its money by collecting user data and monetizing it through the online advertising economy. Google does. Phone users should consider those differences.”
Refrain from sharing photos with faces. Especially considering the ubiquity of facial recognition technology, “when people’s faces are exposed in an image, it is trivially easy for the police to use this technology to identify them,” says Crockford. “I’ve stopped posting videos from protests because of the danger that police or federal agencies will use these publicly posted videos to amass intelligence files on protesters.” It’s not always necessary or safe to take and share such footage, and before posting anything you should consider what its value is. Of course, some images are crucial catalysts for accountability, conversation, and change—such as the very video that sparked many of the most recent demonstrations, that of a Minneapolis police officer fatally kneeling on George Floyd’s neck for nearly nine minutes. Still, before posting a photo make sure to carefully block out any faces or easily identifiable features, like tattoos. You can either obscure those aspects, or use a secure blurring tool. Crockford recommends the Guardian Project’s ObscuraCam app, which is available on Google phones.
This responsibility falls especially on journalists who are attending protests to cover them. “Reporters should be aware that images they publish could be used to harm people,” she notes. “They should be aware that face surveillance technology has profoundly changed what it means to be depicted in a public image, and act accordingly.”